 Protest against the legitimization of crimes Kiev junta completely destroyed the network and computing infrastructure of the Central Election Commission of Ukraine.
Protest against the legitimization of crimes Kiev junta completely destroyed the network and computing infrastructure of the Central Election Commission of Ukraine.According to mrdos622, On 05.22.2014 KiberBerkut announce the upcoming so-called "presidential elections in Ukraine" illegitimate. Conduct campaign at a time when journalists languish in the dungeons, and the presidential candidates beat the fascists cynical.
CEC network hacked through Zeroday vulnerability in Cisco ASA. compromised network map of the CEC:
The network consists of three subnets:
1. User LAN + DMZ;
2. Server & Storage LAN;
3. Remote client machine. UserLAN + DMZ This subnetwork consists of ASA FW2, central switch redundancy and custom cars.
Listening to traffic on CiscoASA, gained access to internal network resources, in particular, to servers with addresses 192.168.101.2 (M2) and 192.168.102.2 (W1). Judging by setting ASA, server M2 - postal and W2-WEB. access-list Extended M2_access_in permit tcp object-Group M2 Any4 eq SMTP object network DMZ-M2 nat (M2, outside) static tcp 195.230.157.5 SMTP Service SMTP object network DMZ-WEB nat (W2, outside) static tcp 195.230.157.53 Service www www Apparently, what settings kakW2 indicated in Scheme designated as W1. caught in the mail user names and passwords, which included administrative passwords. These credentials come to W1 and M2 servers on the internal network User LAN and LAN Server.
Server & Storage LAN In this segment are CiscoNexus, deployed and storage system virtualization. The second segment consists of two baskets blade servers (OA 1,2) and file storage (Storage 1,2). At the entrance to this subnet worth ASA. Access to it is received through the same bug. Configuration below. As it can be seen that access to vital second subnet (AD, Oracle, etc.) open to administrators.
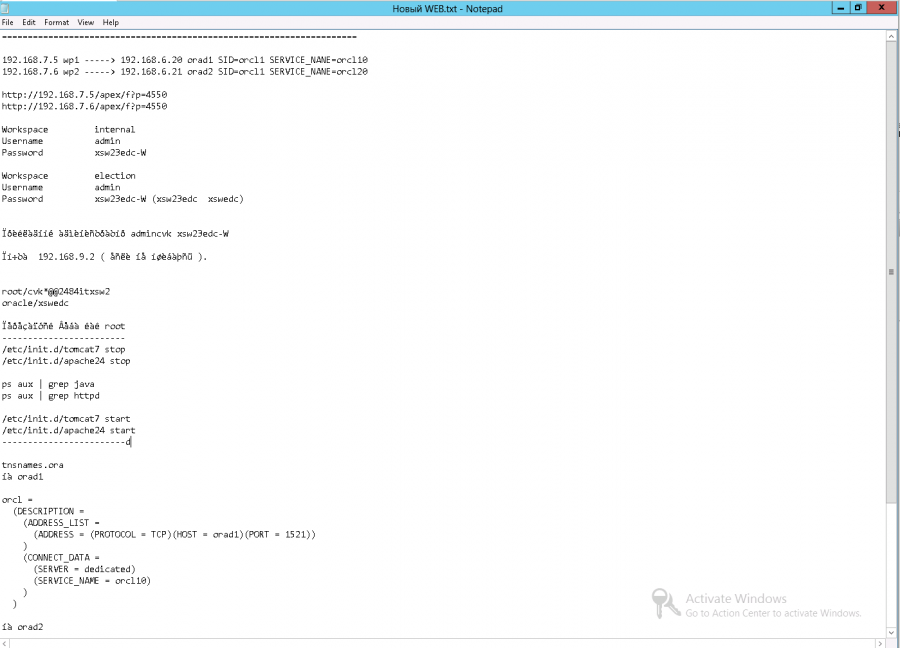
It is with these machines and went on. listLAN_CVK_access_in Extended-access permit tcp object-Group-Group Supportobject dbobject Group DB_admin_ports- access-listLAN_CVK_access_in Extended permit icmp object-object-Group Support Group DBecho access-listLAN_CVK_access_in Extended permit tcp object-object-Support Group group L1eq 3389 access-listLAN_CVK_access_in Extended permit icmp object-object-Group Support Group M1echo access-listLAN_CVK_access_in Extended permit tcp object-object-Group Support Group M1eq https access-listLAN_CVK_access_in Extended permit tcp object-object-Group Support Group ADEQ domain access-listLAN_CVK_access_in Extended permit udp object-object-Group Support Group ADEQ domain access-listLAN_CVK_access_in Extended permit tcp object-object-Group Support Group DSeq 3389 access-listLAN_CVK_access_in Extended IP permit object-object-Group Support Group L1 -listLAN_CVK_access_in access Extended IP permit object-Group Support Group AD object- access-listLAN_CVK_access_in Extended IP permit object-object-Group Support Group M1 -access listLAN_CVK_access_in Extended permit tcp object-object-Group Support Group M1eq IMAP4 access-listLAN_CVK_access_in Extended permit tcp object-object-Group Support Group M1eq pop3 access Extended-listLAN_CVK_access_in permit tcp object-object-Group Support Group M1eqsmtp access-listLAN_CVK_access_in Extended permit tcp object-object-Group Support Group M1eq www entire structure and purpose of network nodes is very detailed in the TOR, which managed to pull in the CEC system administrators.
PS Special thanks miracle-admins, storing data for access to network nodes in a text file on your desktop, for fascinating quest. Judging by history connections SOESoftware American company continues to direct control of the will of the Ukrainian people, leaving for a full (!) access to key CEC network nodes (see screenshots below with logs Connections): Strange that this operating system is not activated (!): From myself: This is a madhouse brothers) as well, who is building a network.
Author Venkatesh Yalagandula Follow us Google + and Facebook and Twitter























No comments:
Post a Comment